Preface
Let's face it. Everyone had some issues with updates in the past. They either start downloading when you're in the middle of something, or they decide to install at night when you left half of your documents open. There's always something when you leave it up to automatic scheduling!
So trying to resolve this pesky annoyance quite a lot of people resort to some drastic measures. They either completely disable updates, or download and install some third-party software that plays various tricks with the Windows update services. In my view, neither of those solutions are ideal.
Disabling updates altogether is a terrible idea, as updates quite often contain bug & security fixes that protect you from malware. And installing some third-party software to control critical infrastructure of the operating system is not something I would want to do either.
Solution
The solution in this case is quite simple and, better still, it is provided and supported by Microsoft - delay installation of updates indefinitely. This is something that has been in Windows 10 Pro since day one. And it is also something that Microsoft don't really want you to know about.
The solution is called Group Policy Objects (or GPOs for short). These things are primarily designed for enterprise users to control their machines from a single location. And their main goal is to impose various (security) restrictions on Windows workstations that are connected to their corporate network.
But what many people don't realize is that those same GPOs are also available on your standalone machine, but albeit in a different manner.
Description
So the idea is to use just two local GPOs to control installation of updates. (You can use more, if you want, but these two will do the minimum work needed.)
- Configure Automatic Updates - will define when to install updates automatically. (In our case never.)
- No auto-restart with logged on users for scheduled automatic updates installations - will define if automatic reboot is allowed if you're installing updates automatically. (In our case, no.)
And that's it. These options are supported by Windows 10 Pro internally. They are used by enterprise sys-admins to control their workstations, and they will remain working in the future.
Steps To Enable
The following steps have to be performed only once:
- Go to the Start menu and type
gpedit.msc. You should see the following app:If you don't see this, then you probably have
Windows 10 Home. In that case, read below. - Right-click
gpedit.mscin the list (that is circled in red above) and pickRun as administratorfrom the pop-up menu. - When the
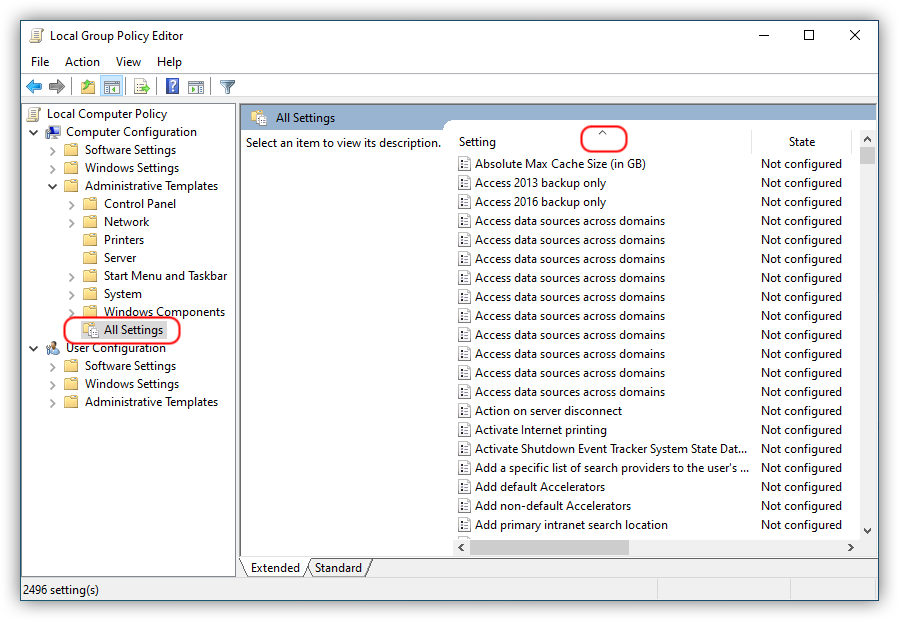
Local Group Policy Editoropens up, navigate to:Local Computer Policy->Computer Configuration->Administrative Templates->All Settingsand click on theSettingcolumn header in the list in the right pane to sort it alphabetically: - Locate "
Configure Automatic Updates" setting in the long list, and double-click it to open:Then make sure to enable it (as I showed above with a red circle), and change the setting to "
2 - Notify for download and auto install".Note that there are other settings in the drop-down list that you may want to choose instead:
- "3 - Auto download and notify for install" - this is the default option, that will apply if you didn't configure this GPO.
- "4 - Auto download and schedule the install" - do everything automatically. (You're probably reading this blog not to do this. 😄)
- "5 - Allow local admin to choose setting" - this won't work on most non-server workstations.
- "7 - Auto Download, Notify to install, Notify to Restart" - this is for the servers only.
You may also want to match the other options with the screenshot above.Click
OKto save changes. - Then locate "
No auto-restart with logged on users for scheduled automatic updates installations" setting in the main list, and double-click it again to open:No auto-restart with logged on users for scheduled automatic updates installations- Windows 10 Pro.Then again enable it and click
OKto save changes.Note that this option technically is not necessary if you selected "2- Notify for download and auto install" in the setting above. It will have effect only if you're allowing automatic updates to proceed, but do not want your computer to restart automatically. I listed it here just for completeness and as a fallback if you enable automatic installation of updates in the first setting. - Lastly, reboot your computer and you're good to go. No more steps necessary.
Now on, your Windows 10 Pro will not install updates, or reboot on its own.
What To Expect Next?
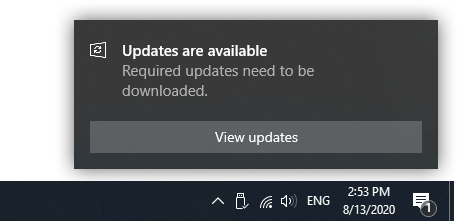
After you've rebooted your computer, Windows update service will now follow instructions from those two GPOs. When it detects an update it will still continue to nag you with one of these pop-ups:
But the main point is that it will not begin installing updates, or worse, reboot your computer in the middle of the night, etc. Just close that pop-up. To install those updates you will have to do it manually. Just like it used to work in Windows 7.
Additionally, you may notice that now on the update screen will have the following message:
*Some settings are managed by your organization
Don't worry, this is normal. There's no organization managing your computer. It's just Microsoft's way of saying that some settings are managed by the GPOs. They are probably showing this because you will not be able to change these via regular controls in the Settings window UI.
Important Caveat
There's one important caveat that I need to point out here.
If you click on the pop-up with an update, that I showed above, and then click Install or Download to began installing or downloading updates,
the GPOs that I listed here will not hold the update service from finishing up the installation and
rebooting your system (in despite of the second GPO that I presented above.) So keep this in mind. In other words, don't touch those update pop-ups until you're
actually ready to commit to it.
Limitations - Windows 10 Home
Well, it can't just work perfectly for everyone, can it? If you're on Windows 10 Home edition, your computer will not have the gpedit.msc console.
Thus you can't do what I described above. 😢 "Thank you", Microsoft!
After I wrote this blog post in August of 2020, we were able to find a solution for the Windows 10 Home users. Please refer to the Windows 10 Update Restart Blocker software.
Rbmm and I looked into the implementation of the Update Service on Windows 10 Home in hopes of finding the System Registry keys that Microsoft uses to control installation of updates in that operating system. Here's what we found so far:
- Unfortunately, Windows 10 Home does not have the implementation to enforce group policy restrictions of the Pro version.
My original hope was that it simply didn't have the
gpedit.mscconsole, but the reality turned out to be worse. It also lacks the code to enforce it. - Thus using any of the following System Registry values (that I see posted in many places online) will not help, as Windows 10 Home doesn't enforce them:
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU] "NoAutoRebootWithLoggedOnUsers"=dword:00000001 "NoAutoUpdate"=dword:00000000 "AUOptions"=dword:00000002 - I also attempted to use another undocumented Registry key that seems to switch Windows 10 Home into a different updating mode:
That setting allowed me to control two different update modes:
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsUpdate\Orchestrator\Configurations] "UsoServicingStack"=dword:00000001CommitAndRebootForFullServicingStackvsCommitAndRebootForLiteServicingStack. But that simply delayed the update and the OS eventually rebooted the computer automatically. - Microsoft seems to be really going gung-ho on installing updates on Windows 10 Home. For instance, there are several places where the system may initiate an
automatic reboot. One is the interactive user process responsible for those "lovely" update notifications,
MusNotificationUx.exe. And if that fails, there's also another place where they try to reboot your system, and that is in the Update Session Orchestrator Service itself.What is also quite unsettling is that they do it in a forced way, meaning that all of your unsaved documents will be lost in the process. They use this API call:
C++[Copy]InitiateShutdownW(NULL, NULL, 0, SHUTDOWN_FORCE_OTHERS | SHUTDOWN_FORCE_SELF | SHUTDOWN_RESTART | SHUTDOWN_RESTARTAPPS | SHUTDOWN_ARSO, //0x2087 SHTDN_REASON_FLAG_PLANNED | SHTDN_REASON_MAJOR_OPERATINGSYSTEM | SHTDN_REASON_MINOR_SERVICEPACK //0x80020010 );See the
SHUTDOWN_FORCE_OTHERSandSHUTDOWN_FORCE_SELFflags. They are the reason why you lose your work. Then they at least try to useSHUTDOWN_RESTARTAPPSflag to restart apps that support restarting after a reboot. But, as practice shows, there are not many non-Microsoft apps that use that feature.Additionally, as you can see they are using a poorly documented flag
SHUTDOWN_ARSO, that has the value of0x2000, in hopes of automatically logging you back in. But that ill-conceived feature with a ton of security ramifications, luckily doesn't seem to be enabled on most systems. (To the point that I couldn't even find a way to test it.)
Final Thoughts
Hoping to find a definitive solution for the Windows 10 Home users to indefinitely delay updates upon their own choosing, Rbmm and I went on with our research. While doing it though, we accidentally stumbled upon a bug in one of the system libraries, that would allow anyone to gain local privilege escalation. Thus we had to put a hold on our current work, and to submit a bug report to Microsoft Security Response Center.
Update: January 9, 2021
Microsoft has refused to fix the vulnerability that we found. Please refer to this and this blog posts for details.